WikiLeaks CIA Vault 7 Releases CherryBlossom Project

 June 15th 2017, WikiLeaks publishes documents from the Cherry Blossom project of the CIA that was developed and implemented with the help of the US nonprofit Stanford Research Institute (SRI International).
June 15th 2017, WikiLeaks publishes documents from the Cherry Blossom project of the CIA that was developed and implemented with the help of the US nonprofit Stanford Research Institute (SRI International).
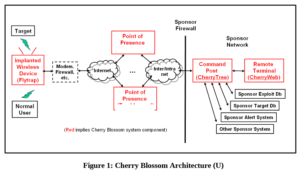
Cherry Blossom provides a means of monitoring the Internet activity of and performing software exploits on Targets of interest. In particular, Cherry Blossom is focused on compromising wireless networking devices, such as wireless routers and access points (APs), to achieve these goals. Such Wi-Fi devices are commonly used as part of the Internet infrastructure in private homes, public spaces (bars, hotels or airports), small and medium sized companies as well as enterprise offices. Therefore these devices are the ideal spot for “Man-In-The-Middle” attacks, as they can easily monitor, control and manipulate the Internet traffic of connected users. By altering the data stream between the user and Internet services, the infected device can inject malicious content into the stream to exploit vulnerabilities in applications or the operating system on the computer of the targeted user.
The wireless device itself is compromised by implanting a customized Cherry Blossom firmware on it; some devices allow upgrading their firmware over a wireless link, so no physical access to the device is necessary for a successful infection. Once the new firmware on the device is flashed, the router or access point will become a so-called FlyTrap. A FlyTrap will beacon over the Internet to a Command & Control server referred to as the Cherry Tree. The beaconed information contains device status and security information that the Cherry Tree logs to a database. In response to this information, the Cherry Tree sends a Mission with operator-defined tasking. An operator can use Cherry Web, a browser-based user interface to view Flytrap status and security info, plan Mission tasking, view Mission-related data, and perform system administration tasks.
Missions may include tasking on Targets to monitor, actions/exploits to perform on a Target, and instructions on when and how to send the next beacon. Tasks for a Flytrap include (among others):
- The scan for email addresses;
- Chat usernames;
- MAC addresses;
- VoIP numbers in passing network traffic to trigger additional actions;
- The copying of the full network traffic of a Target;
- The redirection of a Target’s browser (e.g., to Windex for browser exploitation) or the proxying of a Target’s network connections.
FlyTrap can also setup VPN tunnels to a Cherry Blossom-owned VPN server to give an operator access to clients on the Flytrap’s WLAN/LAN for further exploitation. When the Flytrap detects a Target, it will send an Alert to the Cherry Tree and commence any actions/exploits against the Target. The Cherry Tree logs Alerts to a database, and, potentially distributes Alert information to interested parties (via Catapult).
Leaked Documents
Cherry Blossom: System Req Spec (CDRL-10)
Cherry Blossom: Quick Start Guide
Cherry Blossom: User’s Manual (CDRL-12)
Cherry Blossom: Installation Guide
Editor’s Note:
We humbly seek your support and ask for your generosity in helping us to continue to report to you on news and information you’ll not be getting with the lamestream propaganda media. All our authors have a passion for getting their information out to the general public.
SHARE: To get the word out please copy the article URL to post and comment on your social media platforms. Citizen journalists like myself are under assault by the federal government for they passed anti-Free Speech and Censorship law in the NDAA bill that was signed into law in the dead of night on Christmas Eve, 2016 by Islam Emperor Obama. Free Speech is under attack and NDAA has legalized censorship by Google, Facebook, Twitter, YouTube, Vimeo and most internet platforms because all are globalists and leftists. The establishment republicans are just as dangerous as the democrats, for both are Tyrants! Near all internet hosts suppress and censors articles and videos that do not toe the leftist, globalist and totalitarian line.
COMMENTS: I disabled comments on my articles because the spam was obscene. Each article I wrote was getting around 500 spam comments daily. We have anti-spam software but these spammers spend tons of money to bypass. I guess the Google algorithm does not suppress or censor spam attacks, only prevents them from being seen on key word searches. This site and my articles are SEO optimized but to no avail when trying to out-maneuver the spammers and censor algorithms.
DONATIONS: I am not salaried or compensated for writing and I am fine with that for my passion is distribution of information. I am a Patriot and NewsHawk Network is also. They are a new media site that started in 2017 and I am honored to write for them. They have no income and we row the same boat Passion together. If you like my writing please contribute by going to DONATE. NHN has an income sharing program that is proportionately distributed to authors based upon their overall contribution. Please give as you are able. I have provided a PayPal link below.
REWARDS PROGRAM: We have a rewards program set up to reward all who wish to help us financially. Please visit us at Patreon.com/NHN for details.
Support us monthly on Patreon.com/NHN $1 minimum. Tier program of rewards
Support us with a one-time or annual contribution at DONATE. $12 MINIMUM
View us on Vid.me/newshawknetwork Alternative to YouTube, so far no censoring
FakeBook Alternative: http://Minds.com Join Minds.com; its FREE and unlike Facebook UNCENSORED
Twitter Alternative: http://Gab.ai/NHN Join Gab, its FREE and unlike Twitter UNCENSORED





